Wireless access security mechanism for mobile communication With the popularity of mobile communications and the rapid development of mobile Internet services, mobile networks have become the target of hackers' attention, eavesdropping, camouflage, integrity destruction, denial of service, unauthorized access to services, denial of use / provision, resource exhaustion, etc. Security crimes threaten normal communication services. In order to enable people to enjoy convenient wireless services anytime, anywhere and to obtain information security protection, the wireless access network has proposed a series of security measures such as authentication, authentication, and encryption to deal with it. HuiZhou Superpower Technology Co.,Ltd. , https://www.spchargers.com
3GPP wireless access security
Wireless access security of GSM / GPRS / EDGE system
In the GSM / GPRS / EDGE system, the user ’s SIM card and the home network ’s HLR / AuC share a security key Ki (128bit). Based on this key, the network can authenticate the user, but the user cannot authenticate the network, and the base station The wireless link can be encrypted with the mobile phone.
The authentication and encryption of the GSM / GPRS system is based on the (RAND, SRES, Kc) triplet. The basic process is as follows.
1. When user authentication is required, the MSC / VLR (for circuit domain service) or SGSN (for packet domain service) of the serving network will request an authentication vector from the HLR / AuC to which the user belongs.
2. HLR / AuC first generates a random number RAND, then calculates the authentication response SRES that the mobile station should return based on the RAND and the user's root key Ki according to the A3 algorithm, and uses the A8 algorithm based on the RAND and the user's root key Ki After calculating the key Kc used for encryption, HLR / AuC may also generate multiple sets of such authentication vectors.
3. The HLR / AuC returns one or more (RAND, SRES, Kc) triplets to the MSC / VLR or SGSN of the serving network.
4. The MSC / VLR or SGSN of the serving network initiates an authentication request to the user's mobile phone through NAS (non-access sublayer) signaling. The parameter contains a RAND received in step 3.
5. The mobile phone transfers the authentication request to the SIM card through the RunGSMAlgorithm command. The SIM card uses the A3 algorithm to calculate the authentication response SRES 'based on the RAND and the root key Ki that it securely saves, and uses the A8 algorithm to calculate the encryption key Kc based on RAND and Ki.
6. The SIM card returns SRES 'and Kc to the mobile phone, and also saves Kc in a readable file EF (Kc) on the card.
7. The terminal returns SRES 'to the serving network, and the MSC / VLR or SGSN of the serving network compares it with the SRES received in step 3. If the same, the user authentication succeeds, otherwise it fails. The MSC / VLR or SGSN of the serving network forwards Kc to the base station.
8. When the air interface communication needs to be encrypted, the terminal and the access network of the service area negotiate the encryption algorithm, which is usually called A5 algorithm negotiation. The standard requires that 2G terminals must support the A5 / 1 algorithm and it is recommended to implement the A5 / 3 algorithm.
9. The access network obtains the encryption key Kc from the core network of the service location, the terminal reads Kc from the card, and uses it as the key, calculates the random number with the negotiated A5 algorithm, and then uses it for the air interface message / data Encrypt and decrypt.
3GUMTS system wireless access security
2G access security has the following disadvantages.
1. Only the network can authenticate users, but cannot authenticate users to the network. There may be threats of malicious networks to trick users into login / use, and then steal user information and spread spam / virus information.
2. After passing the PIN code verification (which is very easy to implement), for all RunGSMAlgorithm instructions, the SIM card will calculate the corresponding SRES authentication response according to the random number entered in the instruction, and it is easy for attackers to use it to perform exhaustive Attacks (especially structural enumeration attacks) to reverse the user key Ki.
3. Without integrity protection, there is a threat that messages / data are intercepted and tampered in the middle.
4. Some old algorithms can be replaced by new algorithms with higher security levels.
The 3G system has made targeted improvements to the above deficiencies. In the 3GUMTS (including WCDMA and TD-SCMDMA) system, the USIM card of the user and the HLR / AuC of the home network share a security key K (128bit), based on the secret Key, the network can authenticate the user, and the user can authenticate the network. In addition, the base station and the mobile phone can encrypt and protect the wireless link.
The two-way authentication, encryption and integrity protection of the 3GUMTS system are based on (RAND, XRES, CK, IK, AUTN) quintuples. The basic process is as follows. 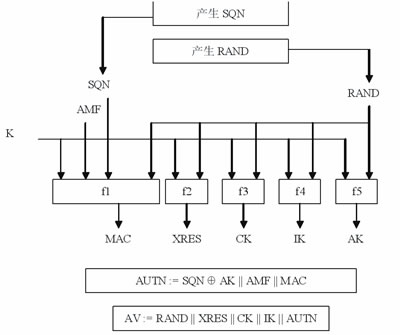
Figure 1 Five-tuple generation method
1. When user authentication is required, the MSC / VLR (for circuit domain service) or SGSN (for packet domain service) of the serving network will request an authentication vector from the HLR / AuC to which the user belongs.
2. HLR / AuC first generates a random number RAND and an SQN, then based on this RAND, SQN and the user's root key K as shown in Figure 1 as follows: use f2 algorithm to generate the mobile station should return the authentication response XRES, Use the f3 algorithm to generate the encryption key CK, the f4 algorithm to generate the integrity protection key IK, and the f1 and f5 algorithms to generate the authentication response AUTN corresponding to the network. HLR / AuC may also generate multiple sets of such authentication vectors.
3. The HLR / AuC returns one or more (RAND, XRES, CK, IK, AUTN) quintuples to the MSC / VLR or SGSN of the serving network.
4. The MSC / VLR or SGSN of the serving network performs the AKA (authentication and key agreement) process through NAS (non-access sublayer) signaling and the user's mobile phone / UISM card.
5. When encryption or integrity protection of the air interface communication is required, the terminal and the access network (RNC) of the service area negotiate and activate the security mode.
6. The access network obtains CK and IK from the core network of the service location, the terminal obtains CK and IK from step 4 or reads from the card, and uses them as keys, and then uses the f8 and f9 algorithms for encryption / decryption and integrity Sexual protection. Integrity protection (IK and f9 algorithm) can also be used to implement simple local authentication between the terminal and the access network.
The above process can also be represented by Figure 2. 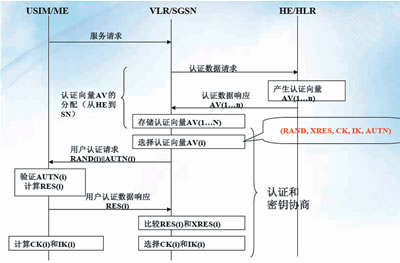
Figure 2 3G UMTS system access security
Wireless access security during 2G / 3G interworking
When the 2GSIM card is connected to the 3G network, in order to avoid requiring the 2G user to change the card to access the 3G network and use the 3G service, the operator usually chooses to allow the user to use the 2GSIM card to access the 3G network. Features.
1.3G terminal can support 2GSIM card interface.
The MSC / VLR and SGSN of the 2.3G service network can communicate with 2GHLR / AuC, and can accept the triple authentication vector.
3.3G terminal and 3G access network support Kc to CK and IK key conversion.
The authentication process at this time is basically the same as the 2G system. The difference is that the MSC / VLR or SGSN of the 3G service network needs to convert Kc to CK and IK through a standard conversion function, and then pass the CK and IK to the 3G service base station. After the terminal obtains Kc from the SIM card, it also needs to convert Kc to CK and IK through the same conversion function; subsequent terminals and 3G serving base stations can use 3G's f8 and f9 algorithms, as well as CK and IK for encryption and integrity protection .
When the 3GUSIM card is connected to the 2G network, in order to use 2G to supplement the 3G coverage and support wider roaming, the operator will also choose to allow users to use the 3GUSIM card to access the 2G network. .
1.3GUSIM card supports conversion function, which can convert XRES 'to SRES' and CK and IK to Kc.
2.3 The GUSIM card supports the 2GSIM interface, so that it can be used by 2G terminals that only support the SIM card. Such a card is usually called a USIM / SIM hybrid card. The SIM interface security algorithm on the hybrid card is based on the USIM security algorithm + conversion function.
3.3GHLR / AuC can support the conversion from quintuple to ternary, so that the ternary authentication vector can be returned to the 2GMSC / VLR or SGSN at the service location.
4. If the service network uses the 2G access network + 3G core network (that is, the BS is 2G, but the MSC / VLR and SGSN are 3G), the MSC / VLR and SGSN should support the conversion of CK + IK to Kc .
When the user uses a 3G / 2G hybrid terminal or a high-end 2G terminal that supports USIM, the USIM function on the hybrid card is used at this time, and the authentication is implemented in the following two situations.
1. When the core network of the service location is 3G, the authentication process is basically the same as the description of the 3GUMTS system. The difference is that the 3GMSC / VLR or SGSN of the service network needs to convert CK and IK to Kc through a standard conversion function, and then Kc is passed to the 2G serving base station; in addition to CK and IK, the hybrid card will also return the Kc generated by the conversion function according to CK and IK to the terminal. The terminal will ignore CK and IK, and only use Kc; if necessary, the terminal and the serving 2G base station can use the negotiated A5 algorithm and Kc for encrypted transmission, but cannot protect the integrity.
2. When the core network of the service area is 2G, the authentication process is basically similar to the description of the 2G system. The difference is that after receiving the authentication vector request from the service area network, the 3GHLR / AuC to which the user belongs first generates a 5-tuple, and then Convert them into triples through standard conversion functions, and then return the triples to the service network; the terminal sends the AuthenTIcate command with GSM security context to the card; the hybrid UISM card first generates XRES, CK, and IK, and then XRES Convert to SRES ', convert CK + IK to Kc, and finally return only SRES' and Kc to the terminal.
When the user uses a lower version 2G terminal that does not support USIM, the SIM function on the hybrid card is used at this time, and the authentication implementation is also divided into two cases.
1. When the core network of the service area is 3G, the authentication process is similar to the 2G system. The difference is that after receiving the authentication vector request from the service area network, the 3GHLR / AuC generated by the user belongs to a 5-tuple and returns It is also a 5-tuple; the 3GMSC / VLR or SGSN of the service network needs to convert XRES to SRES, CK and IK to Kc through a standard conversion function, and then transfer Kc to the 2G service base station; The AUTN parameter will be ignored by the 2G terminal. The 2G terminal only sends the RAND parameter to the hybrid card through the RunGSM Algorithm command; the hybrid card uses RAND and K to first generate XRES ', CK and IK, and then converts XRES' to SRES ' + IK is converted to Kc, and finally only SRES 'and Kc are returned to the terminal.
2. When the core network of the service area is 2G, the authentication process is basically the same as that of the 2G system. The difference is that after receiving the authentication vector request of the service area network, the 3GHLR / AuC to which the user belongs first generates a 5-tuple, Convert them into triples through a standard conversion function, and then return the triples to the service network; the hybrid card first generates XRES ', CK, and IK, then converts XRES' to SRES ', and converts CK + IK to Kc, Finally, only SRES 'and Kc are returned to the terminal.
3 Access security of GPP2 system
Access security of cdma20001x system
In the cdma20001x system, the user's RUIM card and the home network HLR / AC will share a security key A-key (64bit), based on this key, the network can authenticate the user, and the base station and mobile phone can also signal Different encryption methods are used for messaging, voice and data.
The cdma20001x system supports two authentication trigger methods.
1. Global Challenge (GlobalChallenge) implemented by layer 2 function: The service network can set the AUTH field in the access parameter message broadcast on the paging channel to '01', thereby requiring all terminals to use the reverse access channel When sending a message (except Order message, AuthenTIcaTIonChallengeResponse message, Status Response message and Extended Status Response message), the first 64 bits based on SSD (shared safety data), random numbers and specific information field calculation in the message must be carried in the layer 2 parameter field of the message Authentication signature AUTHR.
2. Unique challenge realized by layer 3 function (UniqueChallenge): When needed, the service network can send an AuthenTIcationChallenge message to a specific terminal. The card in the terminal is based on the random number RANDU in the message, and the AUTHU is calculated using the first 64 bits of the SSD and reused The AuthenticationChallenge Response message is returned, and the network then checks whether the AUTHR or AUTHU returned by the terminal is correct. If the HLR / AC shares the SSD with the service network, this check is done by the service network, otherwise the HLR / AC needs to be requested.
SSD (128bit) is a unique design in cdma20001x certification. The introduction of SSD is to avoid excessive use of the user's root key A-key and avoid the need to share the A-key to the service network. SSD generation and subsequent updates can only be performed between HLR / AC and RUIM cards. HLR / AC can choose to share an SSD to the service network and set the life cycle of the SSD, but the RUIM card will not disclose the SSD To the terminal. The SSD update process is triggered by sending an SSDUpdate message to the terminal / card via the network. The message contains a random number RNADSSD. In order to prevent the fake service network from maliciously updating the SSD, the card will generate a random number RANDBS and then the terminal will send it to the network through the BSChallenge Order message. Only when the AUTHBS response returned by the network is correct, the card will use the CAVE algorithm according to A-Key, RANDSSD , UIMID and other calculated values ​​update the SSD. The first 64 bits of the SSD are used for various authentication operations, including the calculation and verification of AUTHR / AUTHU / AUTHBS, which are all calculated using the CAVE algorithm based on the corresponding random number input.
The last 64 bits based on SSD can use CAVE to generate private long code mask (PrivateLCM), message encryption key SMEKey and data encryption key. cdma20001x uses private long code mask scrambling to implement voice encryption; SMEKey key and CMEA (or ECMEA) algorithm to implement signaling message encryption; and data key and ORYX algorithm to implement user data encryption. The terminal and the service network can use Layer 3 messages to negotiate whether to use encryption.
Access security of cdma20001xEV-DO system
In order to support the standard cdma20001xEV-DO access authentication, users need to use a higher version of RUIM card (at least C.S0023Rev.B and later versions of the card), the user's RUIM card and the home AN-AAA will share an HRPD SS ( HRPD shared key, which is of variable length, often takes 128 bits), the card must also be able to support the MD5 algorithm and store the user's ID in EV-DO (called HRPD NAI). Based on the HRPD SS, the network can authenticate users, and messages and data can be encrypted between the base station and the mobile phone.
When the user needs to establish an EV-DO session, during the PPP and LCP negotiation between the terminal and the AN (ie EV-DO base station), the AN will send CHAPChallenge to the terminal. The message contains CHAPID and a random number. The terminal transfers this challenge to RUIM card, the card uses MD5 algorithm to calculate the response based on HRPDSS and random number, and the response is returned to the AN by the card / terminal through CHAP Response, and the AN transmits it to AN-AAA through the A12 interface. SS verifies that the response is correct.
After the terminal has passed the A12 authentication and established an EV-DO session, when the terminal needs to request an EV-DO wireless connection, it can only perform a simpler and faster EV-DO air interface authentication and signing process: the terminal and the network first pass Diffie-Hellman The algorithm establishes a shared session key; the terminal uses the SHA-1 algorithm to sign the packet on the access channel with the session key and time stamp.
The EV-DO system uses the AES algorithm standard to encrypt and protect user data and signaling information; the SHA-1 algorithm is used to implement integrity protection. EV-DO uses a security protocol based on time and counter to generate a password system to generate a changing encryption mask.
1x / EV-DO interoperability for access security
When the EV-DORUIM card is connected to the 1x network, the RUIM card that supports DO access authentication will also support 1xCAVE authentication, and the A-key is kept secret. The EV-DORUIM card will use CAVE certification in a 1x network, just like a 1x RUIM card in a 1x network.
When using a 1xRUIM card to access the EV-DO network, in order for 1x users to access the EV-DO network and use EV-DO services without changing the card, the EV-DO terminal and network need to support the following additional functions.
In order to calculate CHAPResponse, the terminal needs to be able to send a RunCave command to the 1xRUIM card, that is, the CHAP authentication algorithm is actually used in CHAP. The terminal must also be able to generate HRPD NAI based on the 1x ID information in the card.
The AN-AAA on the network side can recognize that the card uses the CAVE algorithm; it provides an additional interface to the HLR / AC corresponding to the card, and can simulate itself as a VLR requesting authentication results and / or SSD from the HLR.