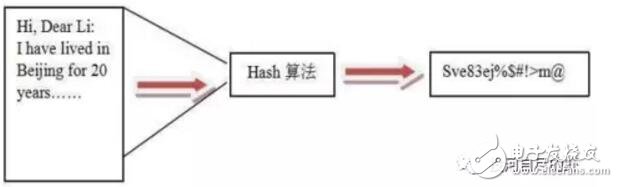
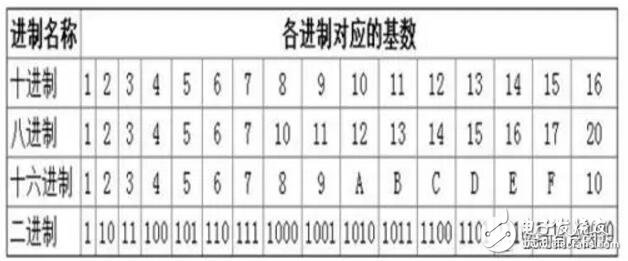
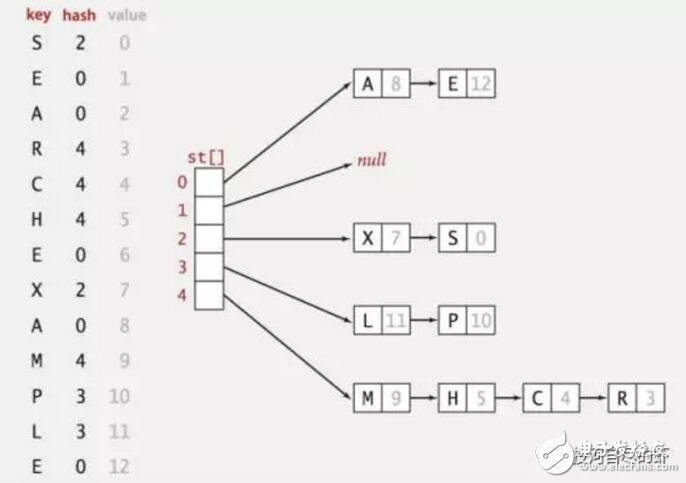
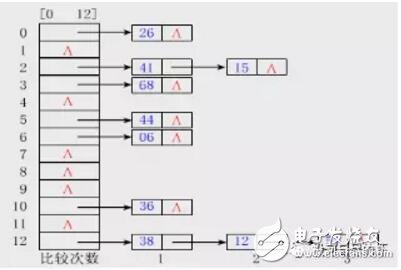
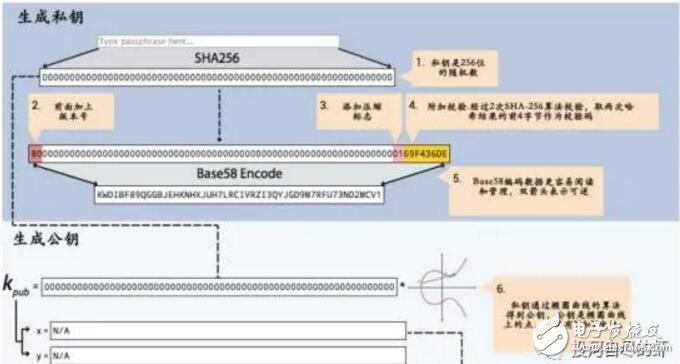
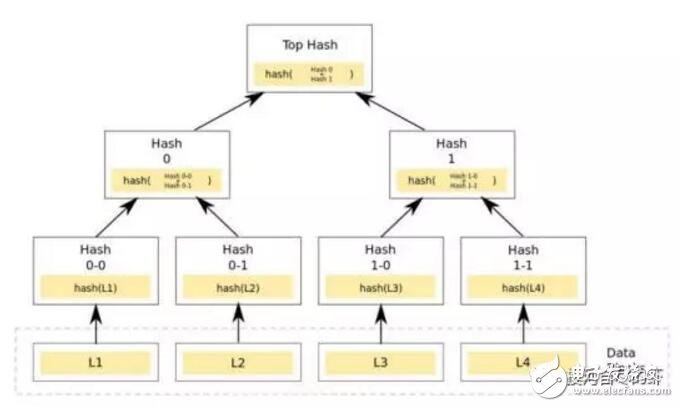
Blockchain technology is a combination of a series of technologies to establish a new technical architecture. The hash algorithm is a particularly important piece. Here is a brief description of the hash algorithm. If there is any misunderstanding, please correct me in time. Before talking about the hash algorithm, first clarify a basic computer knowledge. The computer uses a binary mode at the bottom of the machine code. The so-called binary means that the bottom layer is identified by 0/1. All data transmission records are stored in the mode of 010101. The two states can also be regarded as a switch in daily life, with 1 indicating on and 0 indicating off. Then the smallest unit of data in a computer is the 0 or 1 mentioned here, here we call it bit (bit or bit), 8 bits make up a byte. Of course, there are octal and hexadecimal representations in computers, so I won’t discuss them here for the time being. Only clarify the concept of a binary at the bottom. The Hash algorithm maps binary values ​​of any length to a shorter fixed-length binary value, and this small binary value is called a hash value. The hash value is a unique and extremely compact numerical representation of a piece of data. If you hash a piece of plaintext and even change only one letter of that paragraph, subsequent hashes will produce different values. It is computationally impossible to find two different inputs that are hashed as the same value, so the hash value of the data can check the integrity of the data. Generally used for fast search and encryption algorithms. Introduce the concept of a hash table. In the computer data structure, given a table M, the keyword key, there is a function H (key). For any given keyword value key, after substituting the function into the function, you can get the key The address recorded in the table is called the hash table. A simple understanding of the hash algorithm is this one-way encryption. A plaintext encryption is called a ciphertext, and it is irreversible. There is only an encryption process and no decryption process. Explains the concept of hash function and hash table, so currently commonly used hash algorithms are MD5 (has been cracked), SHA series algorithms (sha-256 algorithm is used in Bitcoin). SHA mentioned here (secure hash algorithm) This is not an algorithm, it is a set of hash functions, and now there are algorithms such as sha-224, sha-256, sha-384, and sha-512. When Satoshi Nakamoto designed Bitcoin in 2009, sha-256 was considered one of the most secure algorithms, so sha-256 was chosen, and it has not been cracked so far. After explaining here, you may think that if the key appears in the same position after calculation in the hash algorithm, conflicts will occur. Here is a brief introduction to the following types of conflict handling. If you are interested, you can check the hash algorithm paper. 1. Zipper method: This method can completely avoid conflicts and link all nodes whose keywords are synonyms in the same singly linked list. If the length of the selected hash table is m, the hash table can be defined as a pointer array t[0..m-1] composed of m head pointers. All nodes whose hash address is i are inserted into the singly linked list with t as the head pointer. The initial value of each component in t should be a null pointer. In the zipper method, the filling factor α can be greater than 1, but generally α≤1. 2. Multi-hash method: Design two or more hash functions to avoid conflicts. This feels relatively unreliable, but in terms of probability, multiple hash functions still reduce the occurrence of conflicts. 3. Open address method: The open address method has a formula: Hi=(H(key)+di) MOD mi=1, 2. .., k (k《=m-1), where m is the table length of the hash table. di is the incremental sequence when a conflict occurs. If the value of di may be 1, 2, 3,. ..m-1, called linear detection and then hashing. If di takes 1, then after each conflict, move backward by 1 position. If the value of di may be 1, -1, 4, -4, 9, -9, 16, -16,. ..k*k, -k*k (k《=m/2), it is called the second detection and then hashing. If the value of di may be a pseudo-random number sequence. It is called pseudo-random detection and then hashing. Hash algorithm functions are classified according to categories: addition hash, bit operation hash, multiplication hash, division hash, table lookup hash, etc. Refer to Baidu Encyclopedia which is more abstract. If you are interested, you can learn more about it. Combined with the blockchain, the hash function is used in many places in the blockchain: 1. Calculation of the address, public key, and private key of the node in the blockchain. Take the address as an example: the public key undergoes a SHA256 calculation, and then performs a RIPEMD160 calculation to obtain a public key hash (20 bytes\160 bits), adds the version information, and performs two SHA256 calculations and takes the first 4 bytes. After putting the hash public key and the version information, it is encoded by base58 to finally get the address. 2. Merkle tree: It is a tree structure in the data structure, which can be a binary tree or a polytree. It has almost the same characteristics as the tree in the data structure. The difference from the ordinary tree is: the leaf nodes on the merkle tree Store the hash value after the hash calculation, and the non-leaf node is the hash value of the string of its corresponding child nodes in series. Used in block header and SPV authentication. 3. In Bitcoin mining, proof of work (pow), the calculation is actually a nonce. When this random number is combined with other hashed data, a value smaller than the specified target (target) is generated. Mining can also understand a fast and irreversible calculation. SHA256 (SHA256 (version + prev_hash + merkle_root + ntime + nbits + x)) "TARGET. 4. Bloom filter in Bitcoin. Bloom filter is based on the quick search of hash function. The problem of client search is solved. The principle is that Bloom filter can quickly determine that a search value must not exist in a specified set, so that a large amount of irrelevant data can be filtered out and unnecessary downloads of the client can be reduced. A brief introduction to the HASH algorithm and the HASH algorithm used in the blockchain. The blockchain is a combination of multiple technologies and a new technical architecture that combines their respective characteristics. The HASH algorithm and encryption technology are self-contained in the blockchain. Credibility and security control provide the basis. The collision of algorithms and the development of quantum computing. The author explained in the previous article on the security of blockchain that the technology continues to develop, and there will definitely be more suitable technology guarantee applications. achieve. Fiber Optic Pigtail,Pigtail Patch Cord,Fiber Pigtail,Pigtail Fiber Optik Huizhou Fibercan Industrial Co.Ltd , https://www.fibercannetworks.com