IoT security is more difficult, chip process tightens protection
The scope of the Internet of Things continues to expand with the progress and development of the times, reaching industries and enterprises to families and individuals. The security of the Internet of Things has become a concern of everyone, technology has improved, and the risk of security has also increased. How to protect the security of the Internet of Things and how to prevent dangerous intrusions.
As the scope of the Internet of Things continues to expand, and even corporate, industrial, and public utility applications are covered, the risks of inadequate IoT security are also rising. But before you want to expand and even bring benefits to the society, you must first ensure the security of the Internet of Things. Otherwise, the risks are too high and the relevant industries will not rush into it.
In response to security issues, the US Department of Homeland Security (DHS) listed the following six principles in November 2016 to address the challenges of IoT security:
Integrate security with design time
̇ Strengthen security updates and vulnerability management
为Based on proven safety practices
Determining the priority of security measures based on potential impact
̇ Enhance the transparency of the Internet of Things
Be careful when you are online
The above principles are quite practical architectures that allow OEMs and users to understand the trust architecture implemented by processors and collocation software. For example, in the previous generations of products, the trusted architecture can help designers create a more secure IoT device, and users can get many benefits from the networked system.
Routers can curb malicious intrusionsThe overall industry clearly does not integrate security into design time. The large-scale attack in 2016 is to use the hardware connection default password and open network service of the networked device. The invasion was not only because of the lack of security of the device, but also because there were no other mitigation measures in the Internet of Things.
Routers located at the edge of the local area network or the Internet are especially suitable for curbing such malicious behaviors. This method entrusts the security of the Internet of Things to the ISP, so it is difficult to implement smoothly. Even if the ISP is not the target of the IoT attack, it is indirectly Affected. As more and more IoT moves to more costly wireless links, ISPs may be more willing to enhance their marginal security.
For network equipment companies and processor vendors, such security practices have long been commonplace, such as beginning with partial filtering of packets based on packetized data, or applying deep packet inspection (DPI), or even using IPsec or SSL. The authentication mechanism of these communication protocols is used to protect the data transmitted by them. Depending on processor performance and network speed, it may speed up the operation of these features.
Another way to deviate from this type of security practice is User/Entity Behavior Analysis (UEBA). This technology further extends the DPI that is often used to track endpoints and their communications, as well as basic heuristics, using machine learning to learn from the vast collection of data that monitors packets to find out abnormal network traffic and determine if it is out of control. IoT devices, data leaks, or financial fraud incidents triggered by thieves. From the customer's field side, UEBA can be implemented in software through a general-purpose processor, and in the future it can be removed to a dedicated machine learning processor.
Responsible IoT developers will implement security at design time, but they must use different methods to select processors. Security, especially platform security, must be considered a prerequisite for component selection.
In addition to network security features, the processor implements platform trust functionality that extends the basic Trusted Execution Environment (TEE) capabilities of the ARM CPU. Such platform trust methods provide security during the life of the device, including the manufacturing, commissioning, operation, update, and decommissioning phases of the device, as well as the entire cycle from power on to shutdown.
As a result, designers can create systems that protect their integrity, according to the US Department of Homeland Security, which uses "integrated security features to enhance the device's own protection capabilities and integrity."
Security updates and vulnerability managementUndoubtedly, security updates and vulnerability management are also weaknesses in the Internet of Things industry. For the average user, the main connection between security and itself is: Will the device or data control be taken away by the hacker?
While smartphones are as vulnerable as IoT devices in this regard, smartphones continue to enhance their security. In 2016, the FBI struggled to extract data from the iPhone, but Apple made the FBI's mission more difficult.
However, Apple's technology, devices and developers of the IoT infrastructure can also be achieved. The trusted platform ensures that only the program code signed by the OEM can activate the device. In addition, it can protect the program code block and the data stored in the device, provide OEMs with building blocks, and limit the program code that can be executed by the device, just like the iPhone can only execute the program code passed by Apple and through it. App store download.
Ideally, IoT devices should be based on a trusted platform and must be zero when shipped. In reality, however, all devices contain errors, and most can be corrected by software. With a trusted platform and security deployment and update tools, even if there are too many errors in the firmware, you can use the special encryption key stored in the chip to update. The idea is to install a new firmware and key while invalidating the old key so that the hacker cannot revert the device to the previously valid firmware image.
Under the issue of security update and vulnerability management, the Department of Homeland Security proposed a vague but thought-provoking proposal: to formulate a shutdown strategy. Should the device be self-decommissioned after a period of use or receipt of an OEM signal? This is certainly possible, as long as the aforementioned safe boot or update procedure is used: the OEM can set up the device program in the factory, let the device stop after a certain time, or push the update to command the device to self-terminate.
Reuse proven security practicesMost technology vendors have always encouraged customers to take advantage of the security features integrated into the product, which is "based on proven security practices." Through a large number of documentation and customer support services, OEMs will be able to take advantage of these features.
In addition, customers who need to customize the function can also use the consulting service, and the relevant vendors also assist in system verification to confirm that the system meets the best practices recommended by organizations such as DHS, NIST and Open Web ApplicaTIon Security Project.
Technology vendors believe that the use of the trust function of the processor platform should be the top priority for IoT designers, given their impact. Many weaknesses will disappear as long as unauthorized code execution is prevented.
Transparency: Transparency allows IoT-related industries to accurately assess trustworthiness. IoT system users must understand the weaknesses hidden in the system, and developers must understand the potential weaknesses of hardware and software components. Even if there are no known weaknesses for review, gaining visibility into the security development process can help to properly assess risk.
The DHS report's discussion of transparency focuses on the supply chain of the Internet of Things, with particular emphasis on the risks of relying on low-cost, readily available software and hardware solutions. Technology vendors play a key role in the supply chain of IoT devices to help OEMs improve transparency. At the beginning of the product's useful life, defining a safe manufacturing model allows OEMs to load signed-out code without relying on confidentiality mechanisms.
Through this mode, the unique and unique ID and Salt are burned into each chip, and then the information is provided to the OEM and its ODM outsourcing manufacturer, as shown in Figure 1. OEMs will generate their own Salt, and the technology supplier will not know the secrets of the OEM, and the OEM will entrust it to the vendor's processor for protection. After all, having transparency doesn't mean sharing all the information.
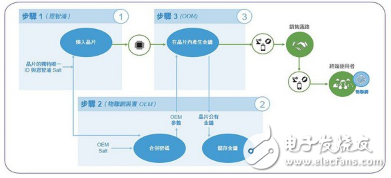
Figure 1: The secure distributed manufacturing model provides transparent security.
For ODM, the processor can generate a unique set of unique public-private keys on Slat. The chip can output a public key but cannot output a private key. The OEM can use the public key to sign the program code and then pass it to the ODM to burn the device.
Once used in the field, the processor will cause the device to verify the program code at boot time and verify with the OEM to ensure that the device has not been copied. The same mechanism applies to security firmware updates and device decommissioning. In summary, the processor allows the device to maintain transparency and integrity throughout its useful life.
At the same time, the technology supplier also clearly states the processor's security declaration, including which functions are out of security, so that the IoT-related industry can assess its trustworthiness.
Be cautious to ensure that IoT devices are not protectedAnother missing thing in the IoT industry is the inadvertent connection of devices to the Internet. Obviously, the device is arguably caused by the device not being properly connected, as these devices are most often accidentally accessed. Who can think of Target's credit card terminal being able to access it remotely via a service company? Who would have thought that the Internet Telnet port on the customer security camera would be exposed to risk?
As mentioned earlier, routers on the customer's site or at the edge of the Internet are in an excellent location for monitoring traffic, setting up network firewalls, detecting intrusions, and analyzing user/entity behavior. As shown in Figure 2, the router can act as a security agent for IoT devices, designing routers with better or more functions, and even performing some work instead of devices.

Figure 2: Prudent online diagram: Security gateway helps protect endpoints
Routers and IoT devices with better design and no limitations can also deploy SSL or IPsec for authentication and rejection of unauthorized network devices.
Tools to protect IoT security are readily available, and whether it is to be used depends on the OEM. In addition, network equipment companies and ISPs need to provide a higher level of security, helping OEMs with less relevant measures to prevent device failure.
A Home Projector that supports WiFi connection, usually an Android system, can connect to the same WiFi to realize screen sharing. In addition to multimedia functions, you can also watch videos, download software and play games online. Mainly focusing on high-quality goods, the projection screen is clear and true, suitable for home, office, teaching, and entertainment
wifi mini home projector,wifi protable home projector,bluetooth mini projector,HD mini projector
Shenzhen Happybate Trading Co.,LTD , https://www.happybateprojector.com